[image-caption title="%20" description="Attendees%20at%20a%20recent%20RC3%20event%20participate%20in%20a%20cybersecurity%20exercise.%20(Photo%20courtesy%20NRECA)" image="/remagazine/articles/PublishingImages/RC3-IL-Summit-brainwriting-4_0868-1024x713.jpg" /]
Tim Lindahl pulled into the parking lot of Wheat Belt Public Power District in Sidney, Nebraska, on a January morning in 2005. He was early for his interview for a manager of information technology position, so he turned off the engine of his pick-up truck, pulled out his laptop, and searched for an internet signal to check emails while he waited.
In 2005, cellular signals were far less ubiquitous than today, even in a town of 6,000 on the panhandle of western Nebraska with an interstate highway close by. But he was in luck; the signal from Wheat Belt’s Wi-Fi network was strong—and unsecured.
Lindahl found that not only could he jump onto the internet signal to access his email; he could freely surf inside the utility’s network.
“I quickly found the server and several computers, one named ‘CFO,’ another named ‘General Manager,’ none of which were password protected,” he says. “I realized that [network protection] was not on their minds, as it wasn’t for most people at that time.”
His discovery provided an opportunity to demonstrate his IT credentials once inside the office.
“I showed them what I had found and gave them some pointers on how to secure that down a little bit,” he says. His interviewers “realized that I could have absconded with every single file they ever had and they would have never known I was there in the network.”
He got the job.
The use and role of information technology has expanded enormously in the 12 years since Lindahl was hired at Wheat Belt. While password management is still a challenge at many co-ops, managing the full range of cybersecurity threats in a utility has escalated far beyond that.
Unlike other aspects of utility functions, it can be hard to measure and evaluate success in cybersecurity, which can complicate decisions on resource allocations. Privacy needs and concerns make it inherently difficult to share information, even within the cooperative family. And implementing cybersecurity actions can require structural and cultural changes within each cooperative, including educating board members about new and fast-changing technologies, acquiring the tools to track and measure cyber-risk, and hiring or developing cybersecurity-savvy IT talent.
The good news is that co-ops large and small are responding to the challenge by nurturing a culture of cybersecurity that, like co-op safety programs, relies on every employee to contribute to the effort. And cybersecurity is increasingly a topic at board meetings, NRECA conferences, and within the broader cooperative community.
[panel title="October%20is%20National%20Cybersecurity%20Awareness%20Month" css-code=".shortpoint-panel-title%20%7Bline-height:%202rem%20!important;%7D%0A.shortpoint-panel-content%20%7B%0A%20%20%20font-size:%201.4rem;%0A%7D" title-bold="true" css_code_compiled=".dynamic-unique-shortpoint-class-name%20.shortpoint-panel-title%20%7B%0A%20%20%20%20line-height:%202rem%20!important;%0A%7D%0A.dynamic-unique-shortpoint-class-name%20.shortpoint-panel-content%20%7B%0A%20%20%20%20font-size:%201.4rem;%0A%7D"]“National Cyber Security Awareness Month” (NCSAM) was created to raise awareness and understanding of basic cybersecurity practices and to recognize the essential role that individuals play in enhancing cybersecurity. NRECA has several events and offerings planned to mark the October event. Look for a series of tools and resources to help co-ops promote cybersecurity awareness internally and externally. These items will be available in August on Cooperative.com as part of the October issue of Straight Talk. In addition, NRECA will co-host a Cybersecurity Summit on October 10 at NRECA headquarters in Arlington, Virginia. The event will offer techniques and resources for protecting your cooperative against the most common cyber threats and strengthening your cyber-resilience. The event is free and open to NRECA members. [/panel]
RC3
 Communication-based technologies are now integrated into every facet of a cooperative’s business, and securing those technologies from cyberthreats will help safeguard the financial security and welfare of the co-ops and their members, and the integrity of the electric grid. Helping cooperatives build stronger cybersecurity programs is the goal of the Rural Cooperative Cybersecurity Capabilities Program (RC3), launched by NRECA in 2016 with U.S. Department of Energy funding and managed by the association’s Business and Technology Strategies (BTS) team.
Communication-based technologies are now integrated into every facet of a cooperative’s business, and securing those technologies from cyberthreats will help safeguard the financial security and welfare of the co-ops and their members, and the integrity of the electric grid. Helping cooperatives build stronger cybersecurity programs is the goal of the Rural Cooperative Cybersecurity Capabilities Program (RC3), launched by NRECA in 2016 with U.S. Department of Energy funding and managed by the association’s Business and Technology Strategies (BTS) team.
The program is developing tools, resources, and training opportunities to help co-ops build stronger cyberdefenses and increase their resiliency to cyberattacks like ransomware.
Led by Cynthia Hsu, manager of cybersecurity programs at BTS, the RC3 Program held a series of Cybersecurity Summits around the country this year. More than 100 cooperative members participated in the January, April, and May summits, and each was hosted by a leading university or national energy lab conducting cybersecurity research. At the heart of each one-day event was a peer-to-peer exchange among cooperative employees on the key challenges they face.
Below are some of the highlights from the summit discussions.
An engaged board
Hsu says one particular message came through loud and clear from summit participants: An engaged board and supportive CEO makes all the difference.
Lindahl, who is now Wheat Belt’s general manager, says the foundation for a strong cybersecurity program was in place before he arrived.
“I’ve had the luxury of having a very technology-adept board ever since I was hired,” he says. “Twelve years ago, they saw that we really needed to make better use of the technology we have and pay attention to it. Having a board that was engaged since the beginning has made my life a lot easier.”
Brian Heithoff, CEO of High West Energy in Pine Bluff, Wyoming, and an attendee at the first summit, agrees.
“Boards take a lot of pride in being good stewards of the co-op’s well-being today and in considering how to innovate for the future,” he says. “My board has displayed considerable foresight when it comes to protecting our cyber assets, and I appreciate their leadership.”
[panel title="A%20Three-Step%20Approach%20to%20Prepare%20for%20a%20Cyberattack" css-code=".shortpoint-panel-title%20%7Bline-height:%202rem%20!important;%7D%0A.shortpoint-panel-content%20%7B%0A%20%20%20font-size:%201.4rem;%0A%7D" title-bold="true" css_code_compiled=".dynamic-unique-shortpoint-class-name%20.shortpoint-panel-title%20%7B%0A%20%20%20%20line-height:%202rem%20!important;%0A%7D%0A.dynamic-unique-shortpoint-class-name%20.shortpoint-panel-content%20%7B%0A%20%20%20%20font-size:%201.4rem;%0A%7D"]Ed VanHoose, general manager of Clay Electric Cooperative in Illinois, suggests that small cooperatives like his take a three-step approach to respond to and recover from a cyberattack:
1. “Know what you can do about what you don’t know.” Deploy in-line intrusion prevention systems that can detect so-called “zero day threats,” which can be revealed by pre-attack patterns.
2. Have a breach plan that includes regular data back-ups that are stored in locations not connected to your network.
3. Have a way to recoup losses. “You need to know your financial exposure and the cost of protecting your data and your system,” VanHoose says, adding a cybersecurity insurance policy “will pay off in the long run.”[/panel]
Managing risk starts with awareness
“In general, boards easily get the financial and operational risk of something that threatens the co-op’s distribution lines,” says Heithoff. “They have a harder time gauging the possibility that the co-op’s IT system will be hacked.”
He says many think, “We’re a small utility in the middle of rural America. Why would they target us when they have Citibank and ExxonMobil to go after?”
Mark Hayden, CEO of Missoula Electric Cooperative in Missoula, Montana, is working to correct this misperception.
“It’s not about being on anyone’s radar. The bad guys are throwing out a wide net looking to see who they can snag,” he says. “They may not necessarily be targeting Missoula Electric Co-op, but if they find a crack, they’ll exploit it.”
Lindahl adds that one of the challenges in pursuing cybersecurity awareness is that success is the
absence of an event.
“The measurement of what cybersecurity can be is in the thing that never happens. And how do you measure what doesn’t happen?”
Who ‘owns’ cybersecurity?
Hsu says defining who at a co-op “owns” cybersecurity is an important part of developing a cybersecurity plan.
“Cybersecurity is a risk-management strategy which [belongs to] everybody,” says Lindahl. “Yes, cybersecurity is an IT function, but it goes far beyond that. IT just carries out the strategy.”
He says at Wheat Belt, cybersecurity is handled much like safety, where everyone is responsible.
“We do monthly security updates for our directors, and we talk about it extensively in our weekly staff meetings,” he says. “Can I say with absolute confidence that one of our guys won’t get hurt tomorrow? No. But we haven’t had anyone injured in 10 years because we’ve focused on safety. With cybersecurity you can create a good culture, put in the right policies and procedures, the layers of risk protection, and prevent 95 to 98 percent of the intrusions you might otherwise experience.”
Hayden says Missoula Electric looks at it the same way: “We have elevated cybersecurity to a core value at our co-op. We need leadership and support from the board, and the CEO has to be all-in. But while I’m responsible, the entire staff, the linemen, the front office, everyone has to lead by example. It’s risk mitigation done by each of us.”
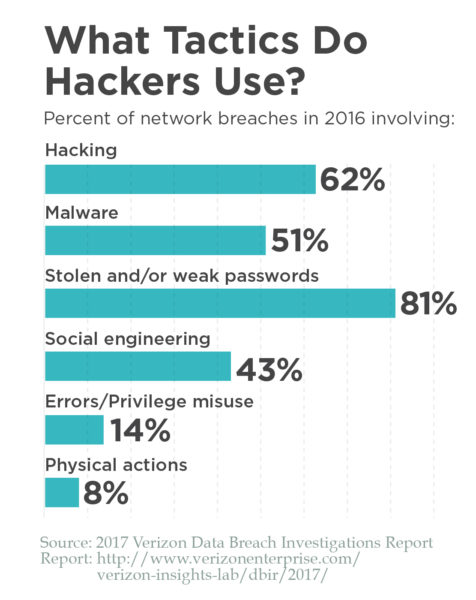
[image-caption title="%20" description="Infographic:%20Password%20Length" image="/remagazine/articles/PublishingImages/Ransomware_Explosion_Web_Password-Length-1024x212.jpg" /]
Cybersecurity resources for small utilities
RC3 summit attendees expressed a strong desire for resources that are specifically designed for cooperatives and for smaller utilities. As one participant explained, “One of the biggest challenges for small IT staffs is just knowing where to start.”
Hsu says existing resources can be complex or theoretical, making it hard for utilities with limited staff resources to translate the information into prioritized actionable steps.
Co-op representatives at the summits also expressed a range of concerns about sharing information. This includes the risk of information about a cybersecurity vulnerability or incident falling into the wrong hands; fear of repercussions if a security breach were revealed; uncertainty about how to differentiate between an actual vulnerability and a benign communication; and lack of clarity on when and where to report an incident.
Lindahl says that despite these uncertainties, it’s more important than ever for co-ops to find ways learn from one another and share ideas and experiences.
“There are certain practices that we won’t allow outside our walls just for our protection,” he says. “But there are a lot of things that we can share, simple things that everybody can do that won’t harm the organization if they get out.”
[panel title="Being%20Small%20is%20Not%20Enough" css-code=".shortpoint-panel-title%20%7Bline-height:%202rem%20!important;%7D%0A.shortpoint-panel-content%20%7B%0A%20%20%20font-size:%201.4rem;%0A%7D" title-bold="true" css_code_compiled=".dynamic-unique-shortpoint-class-name%20.shortpoint-panel-title%20%7B%0A%20%20%20%20line-height:%202rem%20!important;%0A%7D%0A.dynamic-unique-shortpoint-class-name%20.shortpoint-panel-content%20%7B%0A%20%20%20%20font-size:%201.4rem;%0A%7D"]You only need to look at data from the National Small Business Association (NSBA) to know that criminals are targeting small businesses. “Even a simple cyberattack can effectively destroy a small business,” said Rick Snow, owner of Maine Indoor Karting, in testimony before a U.S. House committee. He noted that a recent NSBA survey found 42 percent of its members had experienced a cyberattack, and in 75 percent of those cases, it took more than a day for the issue to be resolved.A 2016 study by the Ponemon Institute found that of the 598 companies they surveyed with fewer than 1,000 employees, 55 percent had experienced a cyberattack in the past 12 months. The most common breaches were web-based and phishing/social engineering attacks. [/panel]
Cybersecurity Insert Featured Stories
Main Story: Cyber Cooperation
Defense in Depth: Who Should have Access?
Human Resources' Role in Cybersecurity
Defending Your Co-op's Network: Options and Resources to Help
Taking Stock: A New Tool to Assess Cybersecurity
