
The security office at the power plant, usually a hive of controlled chaos, is now a tableau of eerie stillness. As you step inside, the only sources of light are the flickering screen of a lone operational monitor and the sparse, ghostly beams filtering through a dirt-smudged window. Shadows play across the walls, thrown by the emergency lights that pulse faintly, casting an irregular glow that barely touches the corners of the room.
The air is thick, not just with tension but with the acrid scent of burnt wiring—a pungent reminder of the systems that failed during the cyberattack. It mingles with the lingering odor of stale coffee from a mug overturned in the haste of evacuation, its dark contents now a stain on scattered papers and technical manuals that litter the desks. The once orderly arrangements are in disarray; chairs are askew, papers flutter slightly with each movement, and a single, flickering monitor casts an unsteady light over a log file filled with foreboding entries.
The low hum of the backup generator provides a constant, almost soothing drone that belies the urgency of securing the facility. It's occasionally punctuated by the crackle of static from an idle radio transceiver, once the lifeline to external security patrols, now silent but for the intermittent bursts of white noise.
As you navigate through the clutter, each step is cautious, the floor beneath echoing slightly, a reminder of desolation. It feels as if the very walls are waiting, holding their breath for the next chapter of the crisis to unfold. Every shadow seems to flicker unnervingly as you pass, as though hinting at hidden threats still lurking unseen.
In this room, where the weight of securing the plant’s safety once thrummed through banks of equipment and busy officers, you now stand alone, the responsibility heavy in the air around you. The challenge is clear: to pierce the gloom, sift through the chaos, and restore order before vulnerabilities can be further exploited.
As you search the desk, you notice a log file displayed on the monitor.
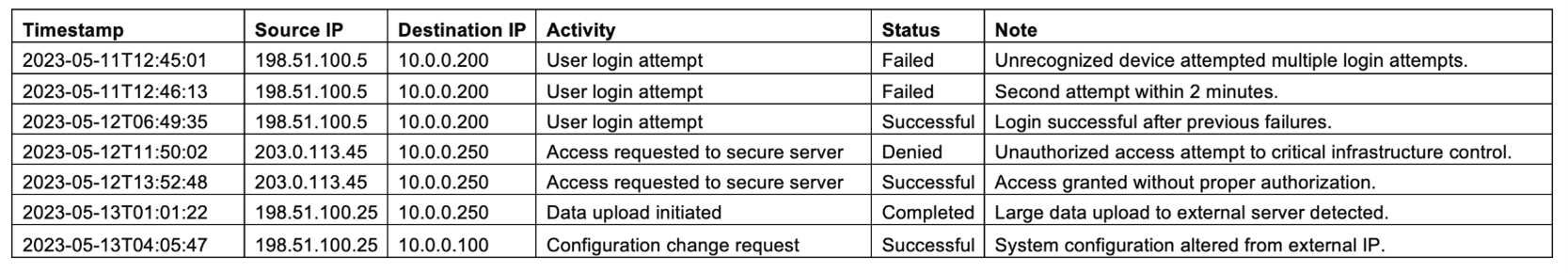
Question 2: Considering the tense atmosphere and compromised security situation, what immediate steps should be taken to secure the security office and mitigate further risks?
[accordions]
[accordion title="Clue"]Talk to Bill, Hillary, or Hugo at the Nozomi booth, they may know crucial details about the breach.[/accordion]
[/accordions]
[row]
[column 3]
[button-coop title="Previous%20Section" link="%2Fconferences-education%2Fmeetings%2FCo-op-Cyber-Tech%2FPages%2FDark-Grid.aspx" /]
[/column]
[column 3]
[button-coop title="Next%20Section" link="%2Fconferences-education%2Fmeetings%2FCo-op-Cyber-Tech%2FPages%2FControl-Room.aspx" /]
[/column]
[column 3][/column]
[column 3][/column]
[/row]
CTF sponsored by:
[row center middle]
[column 4]

[/column]
[column 4]

[/column]
[column 4]

[/column]
[/row]
[row center middle]
[column 4]

[/column]
[column 4]

[/column]
[/row]
