
As you navigate the dimly lit corridors of the power plant, the urgency to secure the facility's digital backbone presses on you. You know you need to apply a critical security patch to the Palo Alto firewall. As you navigate the hallways, a distinct whir of high-pitched fans from servers and switches filters through a slightly ajar door, confirming your suspicions.
The server room stands before you, a crucial vault of the plant's operational intelligence and network security. As you push the door open, the rush of cool air laden with the scent of ozone and metal greets you. Racks of blinking servers and network equipment stretch out in rows, the heartbeat of the facility.
Before you can proceed with the patch you wonder about the assets that might be impacted. After all, a facility like this surely has an asset inventory somewhere, right?
Or do they?
Question 5: What framework mandates maintaining an inventory of all network assets to better manage security risks?
[accordions]
[accordion title="Clue%201"]
You find an interesting paper on the side of one of the server racks. What could it mean?
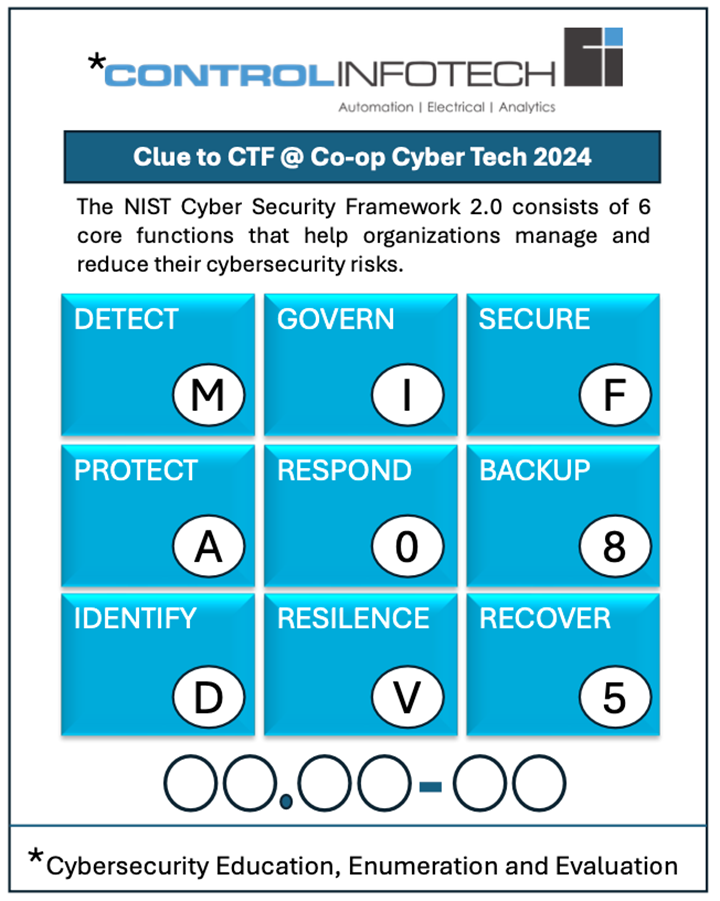
[/accordion]
[accordion title="Clue%202"]
Talk to Control Infotech, they may know crucial details about the breach.[/accordion]
[/accordions]
[row]
[column 3]
[button-coop title="Previous%20Section" link="%2Fconferences-education%2Fmeetings%2FCo-op-Cyber-Tech%2FPages%2FGenerator-Room.aspx" /]
[/column]
[column 3]
[button-coop title="Next%20Section" link="%2Fconferences-education%2Fmeetings%2FCo-op-Cyber-Tech%2FPages%2FInside-Server-Room.aspx" /]
[/column]
[column 3][/column]
[column 3][/column]
[/row]
CTF sponsored by:
[row center middle]
[column 4]

[/column]
[column 4]

[/column]
[column 4]

[/column]
[/row]
[row center middle]
[column 4]

[/column]
[column 4]

[/column]
[/row]
